So a while back OCI got NSGs (Network Security Groups) but most what I still see with implementations is that people tend to use Security Lists.
Remember Security Lists are applied on subnet level while NSGs are applied to VNICs. I recently got following dilemma on tenancy created a while back.
Challenge
- All the subnets were private subnets
- Egress traffic was allowed to 0.0.0.0/0 all ports & protocols in the subnet Security List
- Only private traffic allowed, no egress traffic allowed to public Internet
And the new requirement was to allow traffic only to specific public Internet endpoints, at first I thought not too complicated requirement as we can just create NAT Gateway and route traffic to specific IPs through it.
Second requirement was to control which servers can access the public endpoints. There I thought NSGs would be really helpful together with Security Lists.
Solution
What did work is:
- Changing Security List Egress traffic from 0.0.0.0/0 to VCN only 10.0.0.0/24, and in addition allowing traffic to all OCI Services (see screenshot)
- Route traffic to internet endpoints through NAT GW
- Create NSG which only allows Egress traffic to these specific Internet endpoints and their respective ports
- Associate NSG with compute instance VNICs which require the access
Why I changed the Security List Egress rule to VCN only was that otherwise compute instances in the subnet would have had Egress access to 0.0.0.0/0 even though NSG would have allowed access only to those specific endpoints.
Example
In this demo I’m using OCI Service Status page as the Internet endpoint I want to restrict access.
First I created NAT GW and made a route rule to OCI Service Status page:
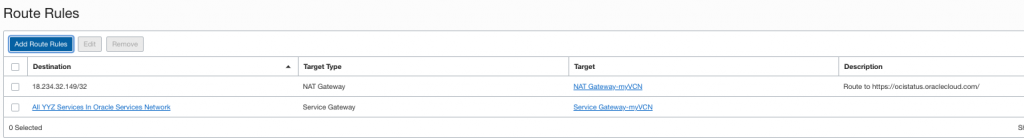
Then I changed Security List Egress rules, I didn’t notice to add access to OCI Services first but quickly noticed yum didn’t work so added that. Now we allow all Egress traffic to my VCN and to OCI Services.
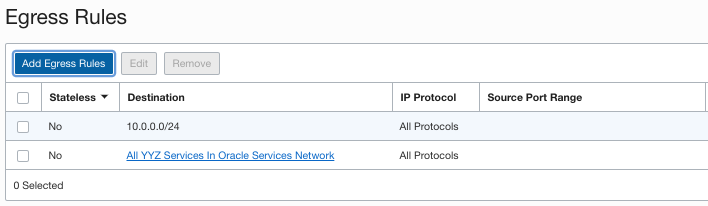
Created NSG which allows Egress traffic to OCI Service Status page:
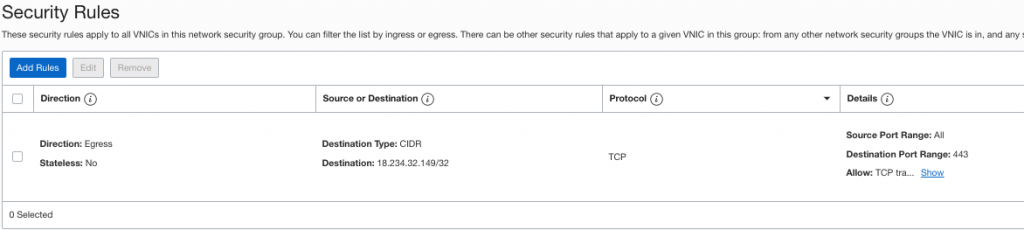
And finally applied NSG to my instance:
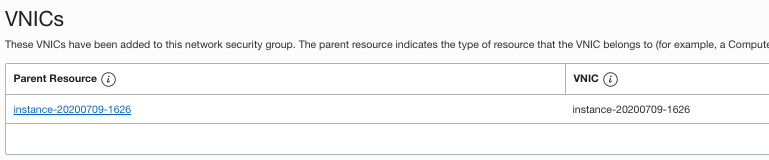
If I login to instance and try to access the web page:
[opc@instance-20200709-1626 ~]$ wget 18.234.32.149:443
--2020-07-09 21:04:59-- http://18.234.32.149:443/
Connecting to 18.234.32.149:443... connected.
HTTP request sent, awaiting response... 200 No headers, assuming HTTP/0.9
Length: unspecified
Saving to: ‘index.html’
[ <=> ] 7 --.-K/s in 0s
2020-07-09 21:04:59 (1.07 MB/s) - ‘index.html’ saved [7]
And same from another instance in the same subnet which doesn’t have NSG applied:
[opc@instance-20200709-1657 ~]$ wget 18.234.32.149:443
--2020-07-09 21:07:58-- http://18.234.32.149:443/
Connecting to 18.234.32.149:443... failed: Connection timed out.
That’s it! Excellent case to use NSGs and Security Lists together!
Hi, I have 1 compartment with 2 instances running. They are on same vcn and vnic. Same security list. But no nsg.
Instance 1 connects to instance 2 on port 3001
Instance 2 connects to 1 on port 3000
Using private ip/internal fqdn or public ip.
Problem is I get error saying no route to host on both instances. Any idea why this is happening.
Hey,
So if you have opened your security lists – do you have firewalld running on the servers (if Linux)?
br,
Simo
how to check if firewall is running or not on Linux machine?
my guess is “no firewall running on linux node”